Secondary Categories: 02 - Infrastructure, 02 - Command and Control
Based on Tim MalcomVetter a secure C2 infrastructure should look like as follows:
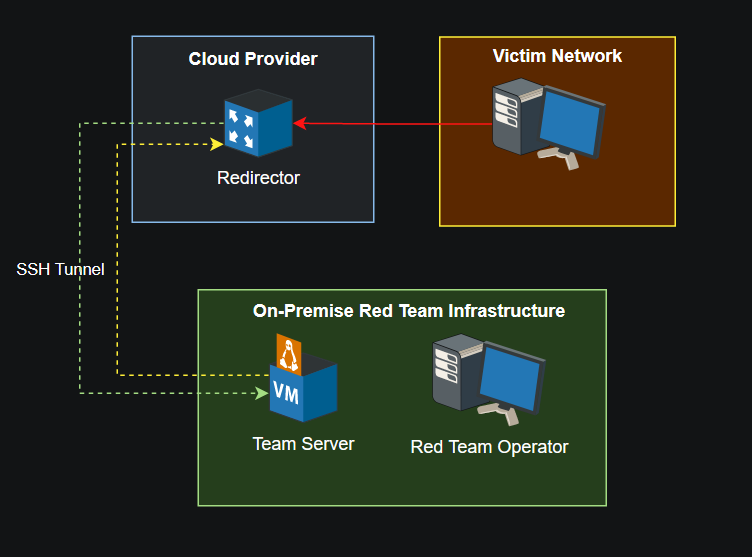 Essentially an SSH (or VPN) tunnel is setup from the C2 server to the HTTPS redirector. It must be done in this direction beacuse:
Essentially an SSH (or VPN) tunnel is setup from the C2 server to the HTTPS redirector. It must be done in this direction beacuse:
- The C2 server should not allow direct access to the internet and only allow access to the redirectors
- If you have HTTPS certificates and need to setup a HTTP redirector you don’t have to place the keys on the redirector if it gets compromised or detected. That way all confidential files are on the C2 server.
No data should be stored on the redirector and should all be maintained on the C2 server. In doing so the client data and C2 traffic will be kept safe from cloud hosting providers. Using a SSH tunnel between the redirector and C2 server allow for traffic to pass in a secure tunnel.
The C2 server should not be ran on a cloud hosting provider and redirectors don’t have to be VMs we can also use CDNs, AWS Lambda, Azure Functions & Cloudflare Workers as serverless redirectors
Implementation
This can easily be done by setting up a remote port forward from the team server to the redirector. If you are using multiple redirectors I suggest using tmux, screen, or another similar tool.
ssh -N -R 8443:localhost:443 -i ssh-user [email protected]We can then confirm the SSH tunnel is working by using curl on the redirector:
curl -v -k https://localhost:8443Red Team Infrastructure Automation
WarHorse
This github repo consist of a fully featured Ansible playbook to deploy infrastructure in the cloud for conducting security assessments. The playbook combines Terraform and Ansible to deploy and configure virtual machines for a wide range of use cases.
Infrastructure Stages
Dropper
Persistent
Interactive
Exfiltration
Payload Staging
There are many different ways to stage payloads or files.
Public Trusted
Below is a list of platforms and sites that can be used to host payloads
- Google Drive
Open Source and Others
- PwnDrop
- Apache (Rewrite Rules)
C2 Frameworks
Most of the C2 frameworks have a way of hosting a file such as:
- Cobalt Strike
- Sliver
Resources:
| Title | URL |
|---|---|
| WarHorse | https://github.com/warhorse/warhorse |