Secondary Categories: 02 - Lateral Movement, 02 - Credential Access
NTLMRelayx
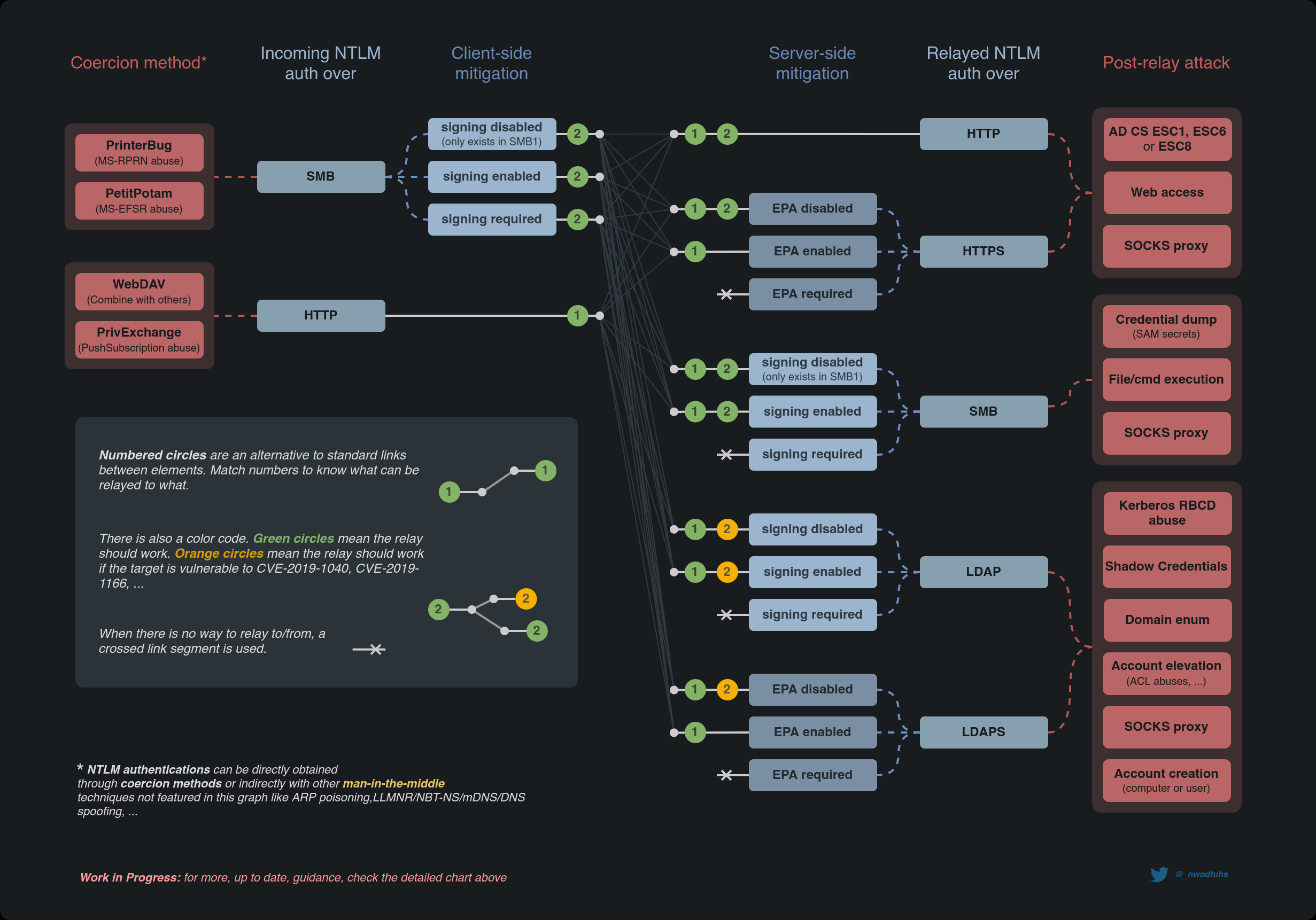
There are several different ways we can leverage credentials we recieved from mitm6, responder, coerced authentication, ect. The chart below from BHIS | Coercions and Relays – The First Cred is the Deepest explains it really well.
- It is optional, but highly recommended to log hashes to a file in addition to the method or tactic used during ntlmrelayx. You can log the hashes to a file use the
-offlag in ntlmrelyx
Resources:
| Title | URL |
|---|---|
| place | holder |