Secondary Categories: 02 - Malware
Description:
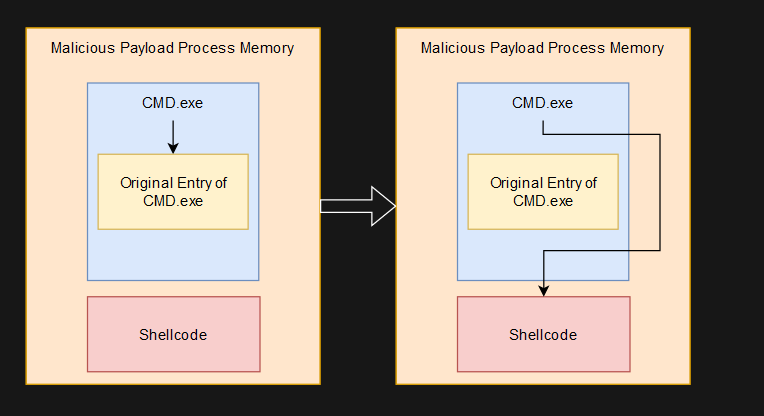
Sometimes the words Dynamic Forking get mixed with the technique called Process Hollowing. This technique is the process of executing another executable file (that is usually trusted) in a suspended state then unmapping the original trusted executable’s image, then followed by a memory allocation. This allows for the possibility to replace an executable that is allocated in the memory space and set the EAX/RAX of the process’s primary thread to the entry point of the replacement executable.
Resources:
| Title | URL |
|---|---|
| Process Hollowing with Mortar | https://0xsp.com/security%20research%20%20development%20srd/defeat-the-castle-bypass-av-advanced-xdr-solutions/ |
| Mortar | https://github.com/0xsp-SRD/mortar |